Like most Network Engineers the COVID-19 Coronavirus has kept me very busy, the push for more and more people to work from home has caused companies to start re-evaluating their VPN Solution and Remote Working solutions. I have over the last couple of weeks performed a few tweaks to customers VPN solutions to allow better use of available bandwidth and to allow more users to connect to the VPN.
Below i will link the solutions i had to implement along with the resources i used and any additional notes which may hopefully help someone else in the same boad.
Extending Current DHCP Scope
The First stumbling block experienced was a simple numbers game, most organisations factor a percentage of users working remotely but when it’s everyone this can cause an issue. Microsoft helpfully don’t provide any easy way to increase the current DHCP Scope to allow more users. Most of the other options available were quite scary involving stopping DHCP Service etc, then came across the below article which after testing on an un-used scope found was really quick and relatively pain free.
https://www.petenetlive.com/KB/Article/0001177
As in the Article, from a Server run the below command to export the Current Configuration of the Scope.
netsh dhcp server \\”Server name” scope “scope subnet” dump>c\:dhcpExport.txt
Example:
netsh dhcp server \\Server-DC01 scope 10.0.0.0 dump >c:\temp\dhcpExport.txtOpen the dhcpExport.txt file using notepad and update the fields required and save as dhcpImport.txt. I Saved this as a second file so that have the original Export to fall back on in the event of any issues.
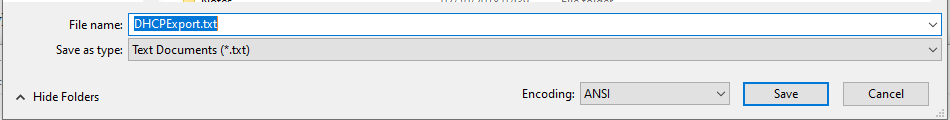
NOTE: when you Save the Export file ensure that Encoding is set to ANSI otherwise the Import will not work.
Then delete the old scope and run the below command to import the scope back in.
netsh exec c:\temp\dhcpImport.txtRefresh DHCP and should now see the DHCP Scope with the new settings and users leases starting to come back into the scope.
Split Tunneling
So you’ve now got all the users on the VPN but you run into the next snag the Internet Circuit is now handling more users than it previously had to and the traffic is increasing. To handle this for one company i had to enable Split Tunneling, where everything comes into the VPN except the traffic I specify, this could also be called local breakout.
IP Based Split Tunneling
Using the above it isn’t made clear that have to use a Standard ACL, i tried this with an Extended ACL but couldn’t get it to work. I believe there is a way to get this to work but haven’t figured out yet (May look into this for a further article!)
DNS Based Split Tunneling
Note on the above, the part it doesn’t tell you is when you get to step 5, under the Group Policy expand Advanced > AnyConnect Client > Custom Attributes, you can then create a mapping of your Custom Attributes to the Group Policy using the name ” dynamic-split-exclude-domains” then picking your Custom Attribute.
